Port Forward Rules: Difference between revisions
Bcarmichael (talk | contribs) |
|||
| (2 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
<span style="display:none" class="helpSource network_port_forward_rules">Port_Forward_Rules</span> | <span style="display:none" class="helpSource network_port_forward_rules">Port_Forward_Rules</span> | ||
{{TriScreenshot|config|network|port-forward-rules}} | {{TriScreenshot|config|network|port-forward-rules}} | ||
Port forwarding is a technique of rewriting the destination address and destination port of packets to send them to a new location. Port forwarding has many uses. The most common use is on networks doing NAT where internal servers have private addresses (ie 192.168.1.100), port forwarding allows the forwarding of traffic to the | Port forwarding is a technique of rewriting the destination address and destination port of packets to send them to a new location. Port forwarding has many uses. The most common use is on networks doing NAT where internal servers have private addresses (ie 192.168.1.100), port forwarding allows the forwarding of traffic to the NG Firewall server's public IP to an internal host. | ||
For example, if the email server is behind | For example, if the email server is behind NG Firewall with a private address (192.168.1.100) and NG Firewall has one public IP (1.2.3.4) which all hosts are "sharing" via NAT to reach the internet, then port forwarding can be used to forward TCP traffic to 1.2.3.4 port 25 (SMTP) to 192.168.1.100 port 25. | ||
Port Forwards Rules work like all rules in | Port Forwards Rules work like all rules in NG Firewall which is described in the [[Rules]] documentation. Rules are evaluated in order on all new sessions. The destination will be rewritten to the ''New Destination'' and the ''New Port'' of the first matching rule. If not rule matches, then no changes are made to the session. | ||
'''If you are having issues with port forwards, it is suggested to follow the [[Port Forward Troubleshooting Guide]]''' | '''If you are having issues with port forwards, it is suggested to follow the [[Port Forward Troubleshooting Guide]]''' | ||
| Line 17: | Line 15: | ||
== Simple Rules == | == Simple Rules == | ||
Simple rules | Simple rules allow for most use cases and avoid extra configuration, which can lead to non-functional forwards. It is suggested to always use simple port forward rules where possible. | ||
[[Image:Network_port_forward_rules_simple.png|thumb|center|A simple port forward]] | [[Image:Network_port_forward_rules_simple.png|thumb|center|A simple port forward]] | ||
| Line 34: | Line 32: | ||
== ''Expert'' Rules == | == ''Expert'' Rules == | ||
There are cases where a more complex | There are cases where a more complex rule is desired, such as: | ||
* forward non TCP/UDP protocols | * forward non TCP/UDP protocols | ||
** Simple Rules can only forward TCP and UDP | ** Simple Rules can only forward TCP and UDP | ||
* changing the new destination port | * changing the new destination port | ||
** Simple Rules only rewrite the destination address | ** Simple Rules only rewrite the destination address. If you also want to change the destination port, expert rules are necessary. For example, forwarding TCP to 1.2.3.4 port 8080 to 192.168.1.100 port 80. | ||
* further limiting what traffic is forwarded | * further limiting what traffic is forwarded | ||
** Expert Rules allow for additional conditions to limit when a port forward will match. For example, you can limit forwarded traffic to traffic from a specific interface, specific IP range, etc. | ** Expert Rules allow for additional conditions to limit when a port forward will match. For example, you can limit forwarded traffic to traffic from a specific interface, specific IP range, etc. | ||
* only to a certain public IP (not all | * only to a certain public IP (not all NG Firewall IPs) | ||
** Simple Rules match all ''Destined Local'' traffic as | ** Simple Rules match all ''Destined Local'' traffic as described in [[Rules]]. If your NG Firewall has multiple public IPs and you only want to forward traffic to one of them you can use Expert Rules. | ||
'''IMPORTANT:''' The reason simple rules are encouraged is that users tend to misconfigure the port forward rule conditions. Adding '''MORE''' conditions means your port forward rule will match '''LESS''' traffic. For example, | '''IMPORTANT:''' The reason simple rules are encouraged is that users tend to misconfigure the port forward rule conditions. Adding '''MORE''' conditions means your port forward rule will match '''LESS''' traffic. For example, you might specify to only forward traffic with "Source Interface = External" and then discover that traffic to a public IP from the internal interface is NOT forwarded because its source interface is NOT external. | ||
[[Image:Network_port_forward_rules_expert.png|thumb|center|A port forward]] | [[Image:Network_port_forward_rules_expert.png|thumb|center|A port forward]] | ||
| Line 58: | Line 56: | ||
** The new destination of the session after the port forward. Typically this is the internal machine like 192.168.1.100. | ** The new destination of the session after the port forward. Typically this is the internal machine like 192.168.1.100. | ||
* New Port | * New Port | ||
** If blank, the new destination port will remain unchanged. If specified all matching sessions will be rewritten to the new destination port. | ** Optional. If blank, the new destination port will remain unchanged. If specified, all matching sessions will be rewritten to the new destination port. | ||
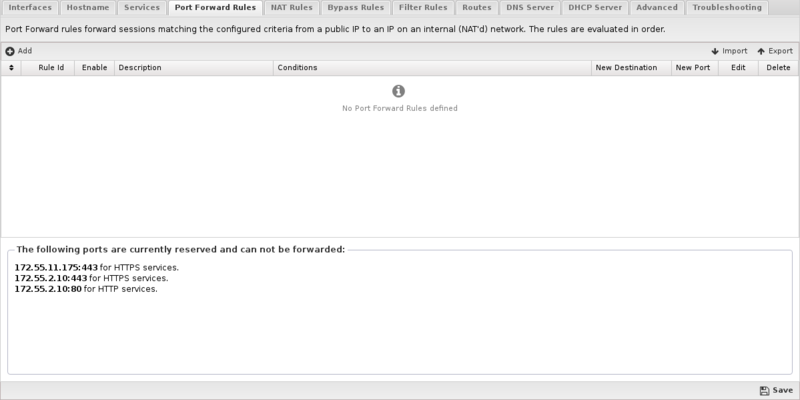
== Reservations == | == Reservations == | ||
At the bottom of the Port Forward Rules tab there is a list of ''reserved'' ports that can not be forwarded because they are currently in use for | At the bottom of the Port Forward Rules tab there is a list of ''reserved'' ports that can not be forwarded because they are currently in use for NG Firewall services. These services can be moved to different ports in the [[Services]] tab if these ports are required for port forwarding. | ||
= Port Forwarding FAQs = | = Port Forwarding FAQs = | ||
{{:Port Forwarding FAQs}} | {{:Port Forwarding FAQs}} | ||
Latest revision as of 16:43, 3 May 2022
Port forwarding is a technique of rewriting the destination address and destination port of packets to send them to a new location. Port forwarding has many uses. The most common use is on networks doing NAT where internal servers have private addresses (ie 192.168.1.100), port forwarding allows the forwarding of traffic to the NG Firewall server's public IP to an internal host.
For example, if the email server is behind NG Firewall with a private address (192.168.1.100) and NG Firewall has one public IP (1.2.3.4) which all hosts are "sharing" via NAT to reach the internet, then port forwarding can be used to forward TCP traffic to 1.2.3.4 port 25 (SMTP) to 192.168.1.100 port 25.
Port Forwards Rules work like all rules in NG Firewall which is described in the Rules documentation. Rules are evaluated in order on all new sessions. The destination will be rewritten to the New Destination and the New Port of the first matching rule. If not rule matches, then no changes are made to the session.
If you are having issues with port forwards, it is suggested to follow the Port Forward Troubleshooting Guide
There are two types port forward rules. To add a Simple Rule click Add Simple Rule. To add a regular rule as described in the Rules documentation click Add.
Simple Rules
Simple rules allow for most use cases and avoid extra configuration, which can lead to non-functional forwards. It is suggested to always use simple port forward rules where possible.
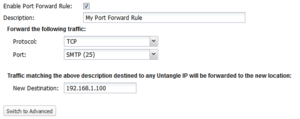
- Enable Port Forward Rule
- If checked, the rule is enabled. If unchecked the rule has no effect and is disabled.
- Description
- A description of this rule. This is just for documentation.
- Protocol
- If "TCP" then only TCP traffic to the specified port is forwarded. If "UDP" then only UDP traffic to the specified port is forwarded. If "TCP & UDP" both TCP and UDP to the specified port is forwarded.
- Port
- This is a list of commonly forwarded ports. Use commas to separate multiple ports, or a dash to denote a range. To specify an arbitrary port, select Other and specify the port.
- New Destination
- The new destination of the session after the port forward. Typically this is the internal machine like 192.168.1.100.
Expert Rules
There are cases where a more complex rule is desired, such as:
- forward non TCP/UDP protocols
- Simple Rules can only forward TCP and UDP
- changing the new destination port
- Simple Rules only rewrite the destination address. If you also want to change the destination port, expert rules are necessary. For example, forwarding TCP to 1.2.3.4 port 8080 to 192.168.1.100 port 80.
- further limiting what traffic is forwarded
- Expert Rules allow for additional conditions to limit when a port forward will match. For example, you can limit forwarded traffic to traffic from a specific interface, specific IP range, etc.
- only to a certain public IP (not all NG Firewall IPs)
- Simple Rules match all Destined Local traffic as described in Rules. If your NG Firewall has multiple public IPs and you only want to forward traffic to one of them you can use Expert Rules.
IMPORTANT: The reason simple rules are encouraged is that users tend to misconfigure the port forward rule conditions. Adding MORE conditions means your port forward rule will match LESS traffic. For example, you might specify to only forward traffic with "Source Interface = External" and then discover that traffic to a public IP from the internal interface is NOT forwarded because its source interface is NOT external.
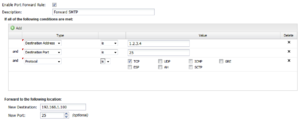
- Enable Port Forward Rule
- If checked, the rule is enabled. If unchecked the rule has no effect and is disabled.
- Description
- A description of this rule. This is just for documentation.
- Conditions
- The conditions describing which sessions will match. As documented in Rules#Condition_List
- New Destination
- The new destination of the session after the port forward. Typically this is the internal machine like 192.168.1.100.
- New Port
- Optional. If blank, the new destination port will remain unchanged. If specified, all matching sessions will be rewritten to the new destination port.
Reservations
At the bottom of the Port Forward Rules tab there is a list of reserved ports that can not be forwarded because they are currently in use for NG Firewall services. These services can be moved to different ports in the Services tab if these ports are required for port forwarding.
Port Forwarding FAQs
Can I specify multiple ports/IPs in one rule?
Absolutely. You can use comma-separated values or hyphen-separated ranges. In the case of IPs you can even use CIDR notation to cover a network space. Keep in mind that NGFW's Debian base limits rules to a maximum of 15 unique values per rule, and that hyphen-separated values count as two values.
My port forward isn't working. Why?
Follow the Port Forward Troubleshooting Guide to see if you can discover the issue.
I setup a port forward for HTTPS (port 443) and it is not working. Why?
Untangle and many of the applications use port 443. In order to forward port 443 you need to move Untangle off of port 443 to a different port. This can be done in Config > Network > Services.
I setup a port forward to my FTP server and it is working but transfers fail. Why?
FTP has multiple connections. If you setup a port forward for the control session (port 21) then you must also setup a port forward for the transfer sessions. You can do this in multiple ways.
- Configure your server to use a range of ports for a transfer, passive ports (i.e 10000-20000) and configure Untangle to forward all of these ports to the FTP server.
- Use 1:1 NAT
Can I port forward traffic destined to a specific hostname like 'mywebserver.com' to a specific server?
No. Packets are destined to IPs not hostnames. When a new packet of a new session arrives from 1.2.3.4 port 1234 to 5.6.7.8 port 5678, the port forward rules must decide if and where to forward that session based on the information present in that packet. This decision can only be made using the information known at this time. If the session is forwarded and its an HTTP or HTTPS session and later it successfully connects, the client may request "mywebserver.com/index.html". At this point in theory the hostname is known, however the port forwards must decide where to forward the session long before the hostname is known. Port forwards rules can not see into the future and know which hostname the client may request at the time the client is trying to initiate the session.
However, This can be accomplished for HTTP and HTTPS traffic using | apache as a reverse proxy. This mechanism will accept all HTTP requests and forward/proxy based on the information in the request and proxy all responses from the final server.
Does Untangle support 1:1 (One to One) NAT?
Yes, Read more about how to setup 1:1 NAT.
What is "Destined Local?"
Destined Local is a flag for port forward rules. It matches on traffic destined to the local untangle machine and one of its IPs. This flag is usually used when you want to redirect a port on the Untangle Server (and all of its IPs) to another server.