Filter Rules
From Edge Threat Management Wiki - Arista
Jump to navigationJump to search
Filter Rules
Filter rules are kernel-level iptables (layer-3) "filter" rules. Filter rules apply to sessions transiting THROUGH the Untangle server. By default this ruleset is blank. Filter Rules are useful for blocking traffic going through the Untangle server.
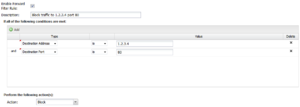
- Enable Filter Rule
- If checked, the rule is enabled. If unchecked the rule has no effect and is disabled.
- IPv6
- If checked, the filter rule will also be active with IPv6 addressing.
- Description
- A description of this rule. This is just for documentation.
- Conditions
- The conditions describing which sessions will match. As documented in Rules#Condition_List
- Action
- Block or Pass. Block means the session dropped silently. Pass means the session will be passed.
The rules are evaluated in order on all new sessions going through the Untangle server as described in the Rules documentation. The action from the first matching rule is taken, if no rule matches the session is passed. All passed sessions are still subject to processing in the Apps.
Why use Filter Rules
There are also block/pass rules available in the Firewall app. There are several key differences that determine when its appropriate to use a Filter Rule vs a Firewall Rule.
- Filter Rules still apply to bypassed traffic. The Firewall doesn't see bypassed traffic. This means if you want to block anything that's bypassed you should use the Filter Rule.
- Filter Rules apply to all protocols while Firewall only sees TCP and UDP. If you want to block IP protocols other than TCP and UDP, you should use Filter Rules.
- Firewall Rules have more application-layer conditions available like Client has exceeded Quota and HTTP: Client User OS. If you need the application-layer conditions you should use Firewall.
- Firewall Rules are evaluated in the Firewall app, so it can be used in policies setup in Policy Manager.