NAT Rules: Difference between revisions
No edit summary |
(No difference)
|
Revision as of 20:17, 31 July 2013
NAT Rules
NAT rules allow the rewriting of the source address of traffic. NAT operation is Untangle is described in Network Configuration#NAT.
Typically NAT is used so that machines on a private subnet (10.*.*.*, 192.168.*.*, etc) can share a single public IP address. To do this when a private machine (say 192.168.1.100) makes a connection to a public server (say google.com) the Untangle server rewrites the source address to the public IP address of Untangle (say 1.2.3.4) on the way out. When return traffic in that session returns to 1.2.3.4 it is rewritten back to the internal address, 192.168.1.100, and forwarded back to the internal server.
NAT
By default "NAT traffic exiting this interface (and bridged peers)" is checked on WAN interfaces which enables the NATing of all sessions exiting that WAN interface with the source address of the primary IP of that interface. In other words, all sessions leaving the External interface will use the External interface's primary IP.
There is also another options called "NAT traffic coming from this interface (and bridged peers)" on non-WAN interfaces. If checked, all traffic coming from the interface will be NATed using the primary IP address of its destination interface.
By default, since only "NAT traffic exiting this interface (and bridged peers)" is checked, NAT is only done on traffic that exits a WAN interface. This means traffic between internal networks will be un-NATed and each can reach each other using the private addresses. If this is not desired, NAT can be done as traffic comes from a non-WAN by checking "NAT traffic coming from this interface (and bridged peers)". This means NAT takes place between local interfaces and no traffic will flow between separate internal networks without explicit port forwards.
Note: checking "NAT traffic exiting this interface (and bridged peers)" adds an implicit NAT rule to NAT all traffic exiting that interface to Auto. It also adds an implicit forward filter rule to block all from that interface that is not to the local server and is not explicitly port forwarded.
Note: checking "NAT traffic coming from this interface (and bridged peers)" adds an implicit NAT rule to NAT all traffic coming from that interface to Auto. It also adds an implicit forward filter rule to block all to that interface that is not to the local server and is not explicitly port forwarded.
NAT Rules
Occasionally additional rules are necessary for more complex NAT setups.
For example, lets assume you have two public IPs 1.2.3.4 and 1.2.3.5. By default you want all traffic to be NATd to the primary address 1.2.3.4, but you want your mail server (192.168.1.100) to send mail from 1.2.3.5. To do this you need to add a NAT rule saying that traffic from the mail server should be NATd to 1.2.3.5. To do so add a rule with Source Address = 192.168.1.100, where NAT Type = 'Custom' and New Source = '1.2.3.5'.
Another, common scenario is setting up 1:1 NAT.
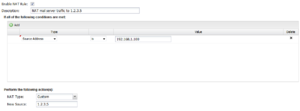
NAT Rules contain several components.
- Enable
- If checked, the rule is enabled. If unchecked the rule has no effect and is disabled.
- Description
- A description of this rule. This is just for documentation.
- Conditions
- The conditions describing which sessions will match. As documented in Rules#Condition_List
- NAT Type
- Auto or Custom. Auto means the session will be NATd to the primary address of the interface which the session exits. Custom allows you to specify a specific IP.
- New Source
- If Custom is selected, specify the IP address that the session will be NATd to.
Like all rules, the NAT rules are evaluated in order. The session will be NATd according to the first matching rule. If not rule matches, the session will be NATd according to the checkboxes in the Interfaces settings. If no rules match and all NAT options in Interfaces are disabled or do not match the session in question, the session is not NATd and it is sent with the original source address.