Spam Blocker
| File:SpamBlocker 128x128.png Spam Blocker |
|
About Spam Blocker
Spam Blocker is an intelligent email filter that identifies and handles spam (unsolicited bulk email). It leverages technology from the SpamAssassin project and improves upon it with the integration of a commercial spam engine. It can scan any email that is transported via SMTP.
Spam Blocker transparently scans email transported over SMTP on the way to your mail server (or outbound if configured so). It does not require any reconfiguration of your DNS MX records or the email server. Any SMTP traffic going through the Untangle server will be scanned.
Settings
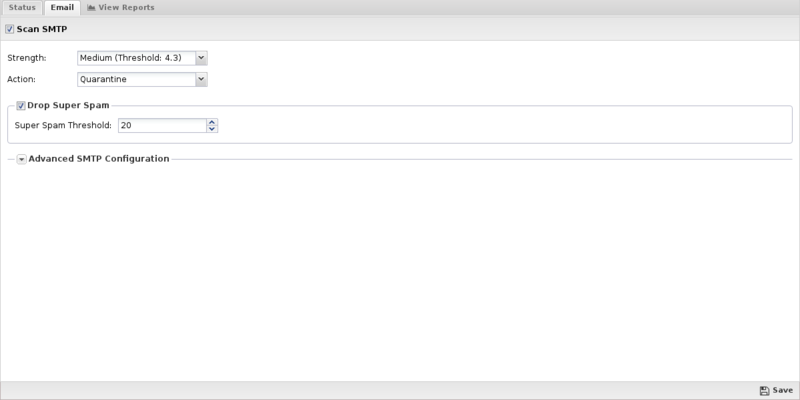
This section reviews the different settings and configuration options available for Spam Blocker.
These settings apply only to the SMTP protocol.
- Scan SMTP: This enables or disables SMTP scanning.
- Strength: If the Spam Score of a message is equal to or greater than this setting your chosen action will be taken on the message. Higher values make Spam Blocker more sensitive to spam. For more information, see What should I set for strength? in the FAQs below.
- Action: The action taken on the message if the Spam Score is high enough.
- If set to Mark, "[Spam]..." will be prepended to the email subject line and it will be delivered. If set to Pass, the message will be delivered as originally sent. Drop will inform the sending server the mail was successfully delivered, but Untangle will drop the mail so it is never delivered. Quarantine will send the mail to users' email quarantine for them to release or delete as they see fit. For more information, refer to Quarantine.
- Drop Super Spam: If this option is enabled, any emails with a score greater than the Super spam score will be dropped.
- Super Spam Score: The score emails must reach to be dropped as Super Spam.
- Advanced SMTP Configuration:
- IMPORTANT: The default values are the suggested values. Changing and customizing settings can easily and will likely cause Spam Blocker to perform less than optimally.
- Enable tarpitting: This option enables Tarpit. If enabled, when an SMTP session is first caught Spam Blocker will check if the client IP is on a DNSBL. If it is, the session is rejected before the remote server is even allowed to send the email. This increases the capacity of a given server by quite a bit and can also save bandwidth, but it can increase false positives if the remote email server has mistakenly been put on a blacklist. This setting will not increase spam scanning accuracy - it will actually decrease it as it will prevent valuable super-spam training data from reaching the spam engine. By enabling this feature you are getting lower spam accuracy, but increased email scanning capacity.
- Enable greylisting: This option enables greylisting. If enabled, each time a new sender tries to send mail to a specific receiver it will receive a "421 Please try again" error. The second time will mail will be allowed. Greylisting will reduce spam because spammers often won't retry transmissions as they should, or the extra time delay will increase the chances of the spam engine properly identifying new spam waves. However, greylisting adds a delay to all legitimate email. This settings is not suggested for most sites because of the complications.
- Add email headers: When enabled, Untangle adds information about the Spam Score and the test run to get that score to the headers of the message.
- Close connection on scan failure: This option will close the connection if the scan fails so the message will be resent and retested. If disabled, a scan failure will allow the email to be delivered without being scanned.
- Scan outbound (WAN) SMTP: If unchecked, outbound mail (mail in sessions going out a WAN interface) will not be scanned. If checked, outbound mail will be scanned just like incoming mail.
- Allow and ignore TLS sessions: This option controls the allowance of TLS sessions. If unchecked (the default) the TLS advertisement (if present) is removed from the server advertisements and TLS is not allowed on any scanned sessions. If checked, the TLS advertisement is allowed and if the client initialized TLS the message will pass through completely unscanned, even if it is spam.
- CPU Load Limit: If your CPU Load exceeds this number incoming connections are stopped until the load decreases. This is specified so that spam scanning can not monopolize the server resources.
- Concurrent Scan Limit: This is the maximum number of messages that can be scanned at the same time. This is specified so that spam scanning can not monopolize the server resources.
- Message Size Limit: This option allows you to change the maximum size of a message that will be scanned for spam. The default maximum size is 256KB. Spam will typically be much smaller, as spammers rely on the sheer number of messages sent. NOTE: this does not control the message size limit of messages passed through Untangle. This does not effect the maximum size of message your server will accept, only the limit on the size of message that will be checked for spam.
Reports
The Reports tab provides a view of all reports and events for all traffic handled by Spam Blocker.
Reports
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
Pre-defined report queries: {{#section:All_Reports|'Spam Blocker'}}
The tables queried to render these reports:
Related Topics
Spam Blocker FAQs
What's the difference between Spam Blocker and Spam Blocker Lite?
Both Spam Blocker and Spam Blocker Lite are based on the SpamAssassin project, however Spam Blocker also integrates a commercial spam engine to boost and improve detection rates.
Why doesn't Spam Blocker block all spam?
There are two main reasons why Spam Blocker might not block all your spam:
- Spam Blocker is a player in an "arms race" against spammers - new techniques are found to get around filters, which are then updated to catch these new methods. No product can reliably block 100% of spam.
- Field testing indicates that our pre-configured Spam Blocker settings, which are conservative in email as spam, are good fit for most organizations. Selecting a more aggressive scan strength setting from the drop-down menu in Spam Blocker is very easy if you'd like, just remember you may get more false positives.
What should I set for strength?
Spam Blocker identifies spam based on hundreds of characteristics. Some example characteristic are emails that begins with Dear, or emails sent with High Priority. Spam Blocker does not mark an email as spam simply because it is sent with high priority; each characteristic is weighted, producing an overall score. Spam Blocker uses this overall score to determine the probability that the email is spam. This overall score is compared to your Strength setting to determine if an email is considered spam.
Spam Blocker's default Strength (Medium) blocks most spam without interfering with legitimate email. If you increase the setting above Medium, Spam Blocker becomes more strict thus catching more spam but also increasing the chance of incorrectly flagging legitimate email as spam (a "false positive"). If you want to catch more spam than is caught with Medium strength and users don't mind sifting through quarantined email to release legitimate email, you can increase your strength to a higher or custom setting. If your organization just wants to cut out most spam, but not have to deal with false positives, then Low may be a better setting.
How can I tell why an email was scored the way it was?
You'll need to take a look at the scoring - you can turn on Add email headers, which will write the spam tests into the headers, or take a closer look at /var/log/mail.info on the command line - when you have a list of tests, you can look up more information on them here.
My CPU load is always above 7. I still need to test for spam. What do I do?
Raising the number will allow you to test for spam, but will likely also increase the CPU load. If your CPU load is that high, that's an indication that your hardware may not be robust enough for your site. If your user count increased since you installed your server, or the volume of the internet traffic has increased substantially, this could be a cause. You may also have been spending as little for hardware as you could get away with. Regardless, you probably also are being impacted in other areas without realizing it. You should determine exactly what the hardware specs are on your server to determine whether you should supplement the existing hardware or replace it with something more robust.
Why do emails with larger attachments sometimes not get delivered?
While NG Firewall is scanning attachments your email server is still waiting for the message, which can trigger a timeout setting. If you're using Exchange, you can try increasing the ConnectionInactivityTimeout setting.
What do the Event Log Actions for Spam Blocker mean?
- pass message - The message was determined to not be spam and was passed.
- mark message - The message was determined to be spam and marked.
- block message - The message was determined to be spam and blocked (silently dropped).
- quarantine message - The message was determined to be spam and quarantined.
- pass Safelist message - The message was passed because the sender was on the user's or global safe pass-list.
- pass Oversize message - The message was passed without being scanned because it was over the spam size limit.
- pass Outbound message - The message was passed without being scanned because it was outbound (WAN-bound).
- block message (scan failure) - The message was blocked because the scan failed and Close connection on scan failure is enabled.
- pass message (scan failure) - The message was blocked because the scan failed and Close connection on scan failure is disabled.
