NG Firewall Virtual Appliance on VMware: Difference between revisions
Bcarmichael (talk | contribs) No edit summary |
Bcarmichael (talk | contribs) No edit summary |
||
| Line 60: | Line 60: | ||
* It is best practice to place your “Management Network “ is on a own vSwitch. (This is not a Must but if you can make sure that NG Firewall does not exist on the same vSwitch as any Management Interface) | * It is best practice to place your “Management Network “ is on a own vSwitch. (This is not a Must but if you can make sure that NG Firewall does not exist on the same vSwitch as any Management Interface) | ||
* On the vSwitches that NG Firewall will connect to activate “promiscuous mode” click on “Properties…” | * On the vSwitches that NG Firewall will connect to activate “promiscuous mode” click on “Properties…” | ||
* Ensure that Promiscuous has status “Accept” otherwise hit "Edit" and go to the “Security “ Tab and change “Reject” to “Accept”. You will need to do this on all vSwitches that NG Firewall Virtual Machine connects to! | * Ensure that Promiscuous has status “Accept” otherwise hit "Edit" and go to the “Security “ Tab and change “Reject” to “Accept”. You will need to do this on all vSwitches that NG Firewall Virtual Machine connects to! | ||
[[Image:vm21.jpg|none|512px|vCenter vSwitch Properties2]] | [[Image:vm21.jpg|none|512px|vCenter vSwitch Properties2]] | ||
Revision as of 19:19, 23 January 2024
NG Firewall can be virtualized through a virtual appliance running on VMware ESX or ESXi.
The virtual appliance can also be used in for demonstrations in VMware player, workstation, fusion, or server, but it is not recommended run a production installation in these environments. Support will help with NG Firewall configuration but configuration of the virtualization hypervisor is beyond the scope of Edge Threat Management support.
- Demo virtual appliance: suitable for installation on a laptop or desktop in order to have a working instance of the platform running inside your Window, OS X, or Linux OS for testing or demonstration purposes. This is supported using VMware Player, Fusion, Server, or Workstation and requires only one physical network interface. Use this mode if you have only one physical network interface in your VMware host machine.
- Production virtual appliance: to be used as a network gateway. This mode requires at least two physical network interfaces (three if you want or need an external DMZ). We recommend you use either VMware ESX or ESXi Server. Use this mode if you have two or more physical network interfaces that you can connect to external, internal and (optionally) DMZ networks.
NG Firewall Support and VMware
Arista Edge Threat Management wants you to have a successful deployment. Unfortunately, our support staff doesn't have the expertise in VMware ESX to ensure that we can help you with installing and configuring VMware. We will certainly help you with your NG Firewall configuration, provided it's running on ESX.
That being said, we'd like to make you aware that systems like NG Firewall that require a lot of real time processing aren't great candidates for virtualization. VMware works by "time-slicing" the physical CPUs in the host system. While the VMware server is off processing other virtual machines, the NG Firewall server is unable to process traffic. At the same time, network traffic continues to arrive. This traffic stacks up and presents itself to the NG Firewall VM as "bursty." This exacerbates any high load issues that may be present. The exact threshold of where it will be unsuitable is hard to say. It is a combination of traffic level, types of traffic, and user expectations.
In summary: We do not recommend virtualizing NG Firewall. If you choose to install NG Firewall in a virtual environment, the support team will assist you with any issues related to the NG Firewall and its applications, but they will not help with virtualization set up/connectivity issues or issues caused by virtualization (high load, slow speeds, etc).
How to install on ESX or ESXi
Before we get started
Requirements:
- VMware ESX server version 6.5.0 Update 3 or newer
- One virtual NIC and vSwitch per NG Firewall Interface
Download the NG Firewall Virtual Machine
- Download the NG Firewall Virtual Appliance:
1. Log into your Edge Threat Management account. 2. Click GET STARTED at the top right-hand corner. 3. Select the latest version and download the ISO file.
Deploy image to ESX server
- Once the image is downloaded, open your VMware vSphere Client and login to your server.
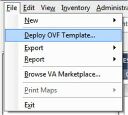
- Once you are logged in, click File -> “Deploy OVF Template…”
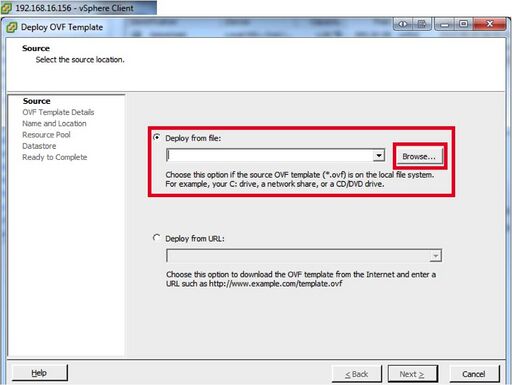
- In the “Deploy OVF Template” wizard mark “Deploy from file:” And hit “Browse…”
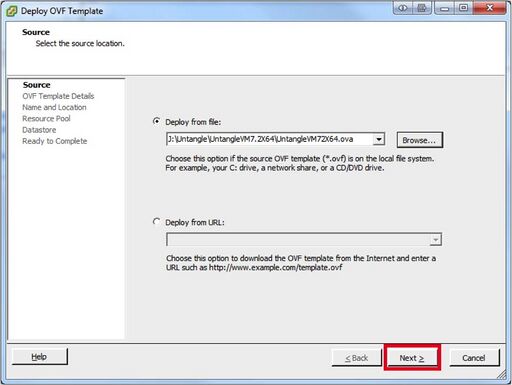
- Browse to the location where you saved your image and click "Open".
- Then hit “Next”
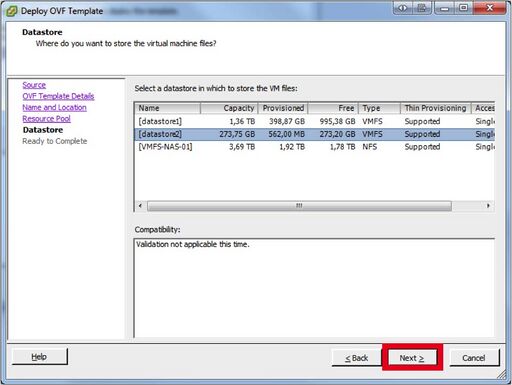
- Read The Template Details and click “Next”.
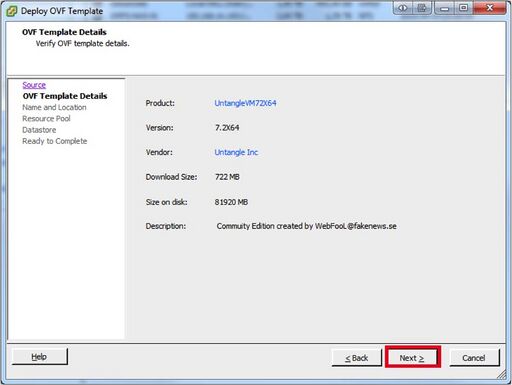
- In the “Name and Location screen” you may either change the name or leave it at the default. Click “Next”.
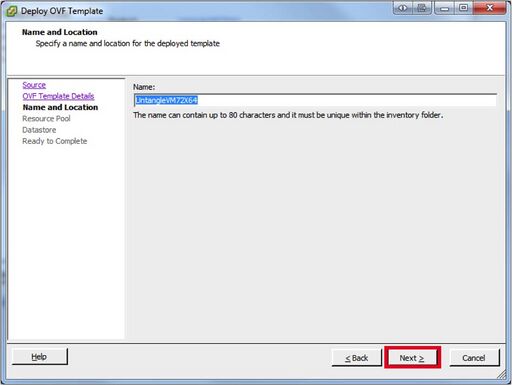
- In the “Resource Pool screen” If you use Resource Pools, select the appropriate pool for the new NG Firewall VM and click "Next". Note: You can always move the VM to another Resource Pool after it's installed.
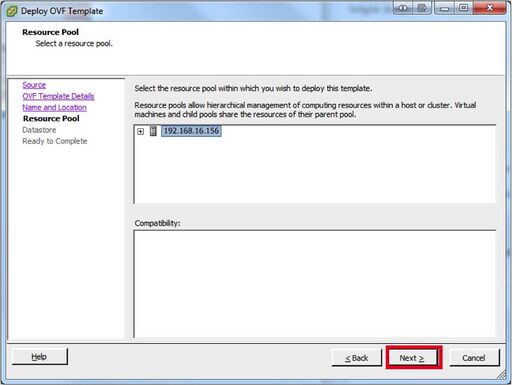
- In the “Datastore screen” Select what datastore you want use click “Next”.
- In the “Ready to Complete” screen, verify that everything looks OK and click “Finish”
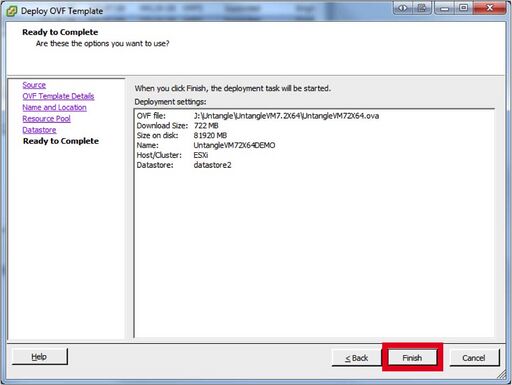
- Wait for the “Deploying” Progress Meter.
- When it is done, Click "Close".
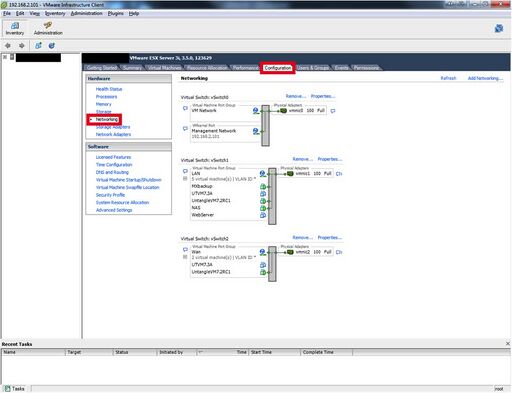
Verify/Configure Physical NIC to vSwitch mappings
- Setup/confirm your vSwitch Settings. Click on the ESX host, then select “Configuration" tab and "Hardware -> Networking”
- It is best practice to place your “Management Network “ is on a own vSwitch. (This is not a Must but if you can make sure that NG Firewall does not exist on the same vSwitch as any Management Interface)
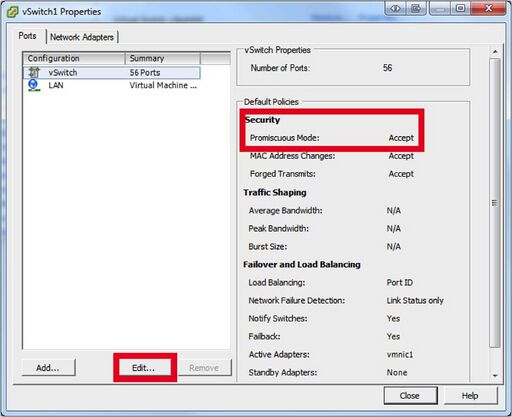
- On the vSwitches that NG Firewall will connect to activate “promiscuous mode” click on “Properties…”
- Ensure that Promiscuous has status “Accept” otherwise hit "Edit" and go to the “Security “ Tab and change “Reject” to “Accept”. You will need to do this on all vSwitches that NG Firewall Virtual Machine connects to!
Configure the Virtual Machine for your Network
- Right click on the new Virtual Machine and select “Edit Settings”.
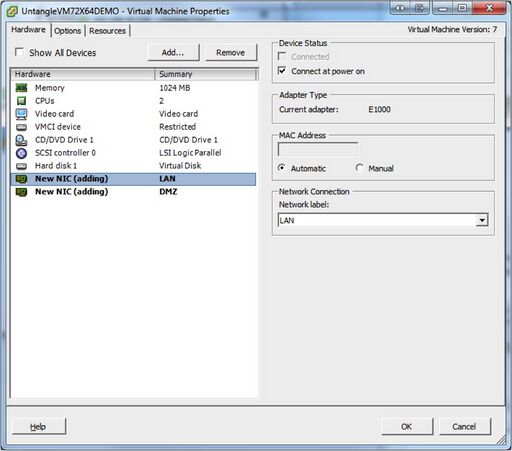
- You will need to add new virtual NICs and connect them to the appropriate vSwitches. Warning! Two Bridged Interfaces to the same vSwitch will crash your ESX server. Each NG Firewall NIC should be connected to its own vSwitch. Each vSwitch should be connected to it's own Physical NIC, or at least be separated by VLAN tagging at the physical NIC level.
- In this example, you can see that the new NICs are connected to different vSwitches labeled LAN and DMZ.
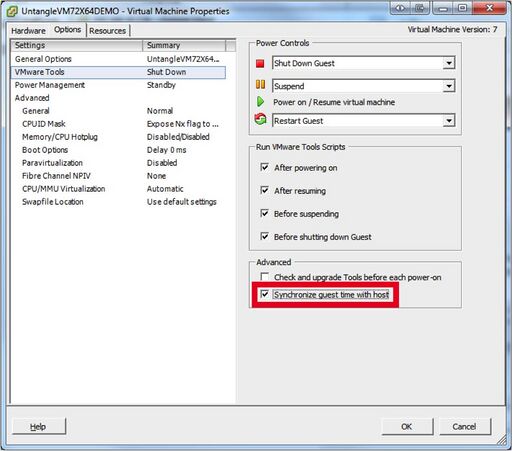
- Under “Options”->“VMware Tools” make sure to check the “Synchronize guest time with host” and click "OK"
Celebrate! You're at the end
Now you are ready to Power on your NG Firewall VM.
More Info and Troubleshooting
For more information on the underlying issues, please see the following:
- Kernel documentation
- VMware documentation
- Microsoft Virtual Server documentation
- Edge Threat Management Community Support
- Edge Threat Management Live Support
For information about using your new NG Firewall software, see our NG Firewall Server User's Guide.