WireGuard VPN: Difference between revisions
mNo edit summary |
mNo edit summary |
||
| Line 48: | Line 48: | ||
{{ServiceAppScreenshot|wireguard-vpn|status}} | {{ServiceAppScreenshot|wireguard-vpn|status}} | ||
=== <u>Settings</u> === | |||
* '''Listen port''' | |||
: Sets the port where the WireGuard server will listen for inbound tunnel connections from peers. | |||
* '''Keepalive interval''' | |||
: Sets the passive keepalive interval which ensures that sessions stay active and allows both peers to passively determine if a connection has failed or been disconnected. | |||
* '''MTU''' | |||
: Sets the MTU size for WireGuard tunnels. | |||
==== <u>Peer IP Address Pool</u> ==== | |||
* '''Assignment''' | |||
: Used to select the method for address pool assignment. Can be set for <b>Automatic</b> to allow the system to automatically select an unused address block or <b>Self-assigned</b> to configure a user selected address block. | |||
{{ServiceAppScreenshot|wireguard-vpn|settings}} | |||
=== <u>IPsec Tunnels</u> === | |||
The IPsec Tunnels tab is where you create and manage the IPsec VPN configuration. The main tab display shows a summary of all IPsec tunnels that have been created. | |||
* ''' Tunnel Editor ''' | |||
: When you create a new tunnel, or edit and existing tunnel, the tunnel editor screen will appear with the following configurable settings: | |||
{| border="1" cellpadding="2" width="85%" align="center" | |||
|+ | |||
! Name !! Description | |||
|- | |||
|width="15%"|'''Enabled''' | |||
|width="70%"|This checkbox allows you to set a tunnel to either enabled or disabled. | |||
|- | |||
|'''Description''' | |||
|This field should contain a short name or description. | |||
|- | |||
|'''Connection Type''' | |||
|This field allows you to set the connection type to any of the following: | |||
*Select Tunnel to specify a host-to-host, host-to-subnet, or subnet-to-subnet tunnel. This is by far the most common connection type. | |||
* Select Transport to specify a host-to-host transport mode tunnel. This connection type is much less common, and would generally only be used if you are attempting to establish an IPsec connection to another host which specifically requires this mode. | |||
|- | |||
|'''IKE Version''' | |||
|The IKE version to use, either version 1 or version 2. Both endpoints must use the same IKE version. | |||
|- | |||
|'''Connect Mode''' | |||
|This field controls how IPsec manages the corresponding tunnel when the IPsec process re-starts: | |||
* Select Always Connected to have the tunnel automatically loaded, routes inserted, and connection initiated. | |||
* Select On Demand to have the tunnel load in standby mode, waiting to respond to an incoming connection request. | |||
|- | |||
|'''Interface''' | |||
|This field allows you to select the network interface that should be associated with the IPsec tunnel on the Untangle server. When you select a valid interface, the Local IP field (see below) will automatically be configured with the corresponding IP address. If for some reason you want to manually configure an IP address that is not currently active, you can set the Interface to Custom and manually input the IP address below. | |||
|- | |||
|'''External IP''' | |||
|Use this field to configure the IP address that is associated with the IPsec VPN on the Untangle server. Normally this field will be read-only and will automatically be populated based on the Interface selected above. If you select Custom as the interface, you can then manually enter the local IP address. | |||
|- | |||
|'''Remote Host''' | |||
|This field should contain the public IP address or DNS name of the host to which the IPsec VPN will be connected. | |||
: '''WARNING''' - Using host names with IPsec tunnels can often cause problems, especially if you have also enabled the L2TP/Xauth VPN server. We '''strongly''' recommend the use of IP addresses in the ''Remote Host'' field. | |||
|- | |||
|'''Local Identifier''' | |||
|This field is used to configure the local identifier used for authentication. When this field is blank the value in the *External IP* field will be used. | |||
|- | |||
|'''Remote Identifier''' | |||
|This field is used to configure the remote identifier used for authentication. When this field is blank, the value in the Remote Host field will be used. | |||
:'''IMPORTANT''' - If the remote host is located behind any kind of NAT device, you may need to use the value <TT>%any</TT> in this field for a connection to be successfully established. | |||
|- | |||
|'''Local Network''' | |||
|This field is used to configure the local network that will be reachable from hosts on the other side of the IPsec VPN. | |||
|- | |||
|'''Remote Network''' | |||
|This field is used to configure the remote network that will be reachable from hosts on the local side of the IPsec VPN. | |||
|- | |||
|'''Shared Secret''' | |||
|This field should contain the shared secret or PSK (pre-shared key) that is used to authenticate the connection, and must be the same on both sides of the tunnel for the connection to be successful. Because the PSK is actually used as the encryption key for the session, using long strings of a random nature will provide the highest level of security. | |||
|- | |||
|'''DPD Interval''' | |||
|The number of seconds between R_U_THERE messages. Enter 0 to disable this feature. | |||
|- | |||
|'''DPD Timeout''' | |||
| The number of seconds for a dead peer tunnel to be restarted. | |||
|- | |||
|'''Ping Address''' | |||
| The IP address of a host on the remote network to ping for verifying that the tunnel is connected and routing. Leave blank to disable. | |||
|- | |||
|'''Ping Interval''' | |||
| The time in minutes between ping attempts of the ping address. Leave as 0 to disable. Recommended value is 1 when using a Ping address. | |||
|- | |||
|'''Authentication and SA/Key Exchange''' | |||
| If you leave the Phase 1 and Phase 2 manual configuration checkboxes disabled, IPsec will attempt to automatically negotiate the encryption protocol with the remote peer when creating the tunnel. Given the number of different IPsec implementations and versions, as well as the overall complexity of the protocol, best results can often be achieved by enabling manual configuration of these two options, and selecting Encryption, Hash, DH Key Group, and Lifetime values that exactly match the settings configured on the peer device. | |||
|} | |||
{{ServiceAppScreenshot|ipsec-vpn|ipsec-tunnels}} | |||
== Reports == | == Reports == | ||
Revision as of 18:56, 13 May 2020
 WireGuard VPN WireGuard VPN
|
|
About WireGuard VPN
The WireGuard VPN service provides virtual private networking via WireGuard, which is an open source lightweight VPN application and protocol designed to be fast, secure, and easy to configure.
The VPN Overview article provides some general guidance of which VPN technology may be the best fit for different scenarios.
Settings
This section reviews the different settings and configuration options available for WireGuard VPN.
Status
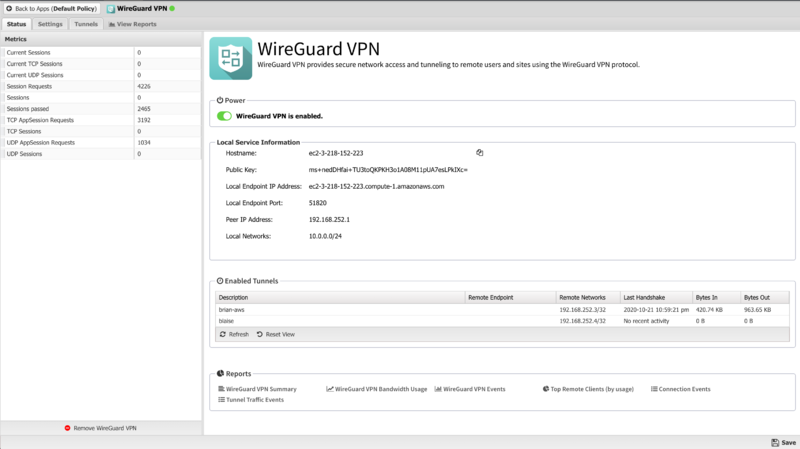
The Status tab shows the status of the WireGuard VPN service
- Local Service Information
- This section displays information about the local WireGuard service such as the public key, endpoint address and port, peer address, and the list of local networks.
- Connected Tunnels
- This section shows a list of active WireGuard tunnels.
Settings
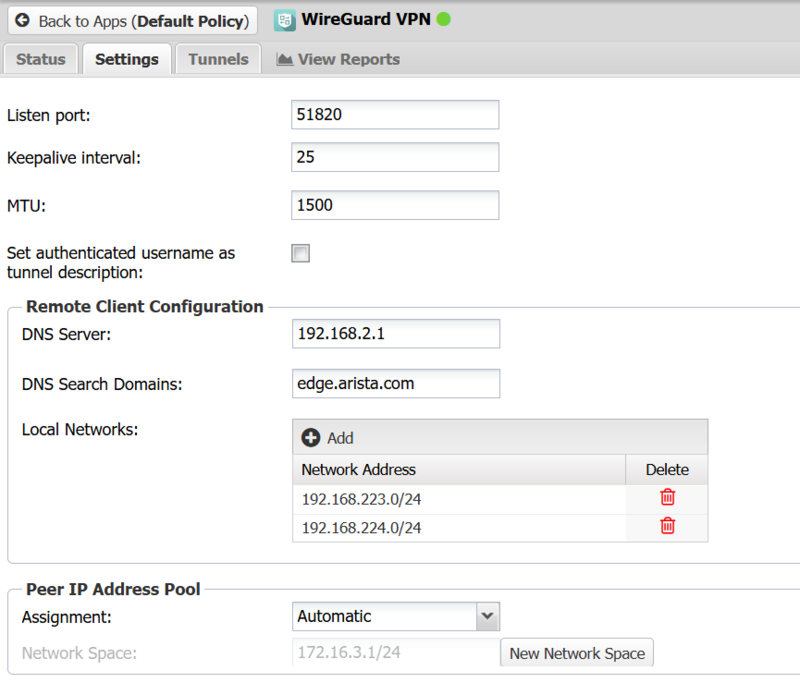
- Listen port
- Sets the port where the WireGuard server will listen for inbound tunnel connections from peers.
- Keepalive interval
- Sets the passive keepalive interval which ensures that sessions stay active and allows both peers to passively determine if a connection has failed or been disconnected.
- MTU
- Sets the MTU size for WireGuard tunnels.
Peer IP Address Pool
- Assignment
- Used to select the method for address pool assignment. Can be set for Automatic to allow the system to automatically select an unused address block or Self-assigned to configure a user selected address block.
IPsec Tunnels
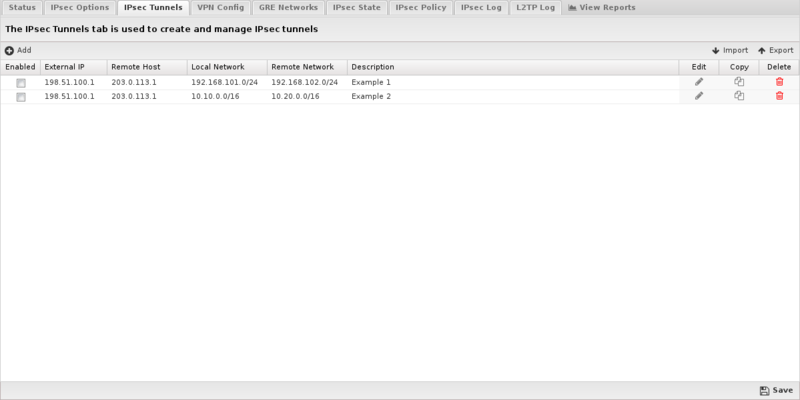
The IPsec Tunnels tab is where you create and manage the IPsec VPN configuration. The main tab display shows a summary of all IPsec tunnels that have been created.
- Tunnel Editor
- When you create a new tunnel, or edit and existing tunnel, the tunnel editor screen will appear with the following configurable settings:
| Name | Description |
|---|---|
| Enabled | This checkbox allows you to set a tunnel to either enabled or disabled. |
| Description | This field should contain a short name or description. |
| Connection Type | This field allows you to set the connection type to any of the following:
|
| IKE Version | The IKE version to use, either version 1 or version 2. Both endpoints must use the same IKE version. |
| Connect Mode | This field controls how IPsec manages the corresponding tunnel when the IPsec process re-starts:
|
| Interface | This field allows you to select the network interface that should be associated with the IPsec tunnel on the Untangle server. When you select a valid interface, the Local IP field (see below) will automatically be configured with the corresponding IP address. If for some reason you want to manually configure an IP address that is not currently active, you can set the Interface to Custom and manually input the IP address below. |
| External IP | Use this field to configure the IP address that is associated with the IPsec VPN on the Untangle server. Normally this field will be read-only and will automatically be populated based on the Interface selected above. If you select Custom as the interface, you can then manually enter the local IP address. |
| Remote Host | This field should contain the public IP address or DNS name of the host to which the IPsec VPN will be connected.
|
| Local Identifier | This field is used to configure the local identifier used for authentication. When this field is blank the value in the *External IP* field will be used. |
| Remote Identifier | This field is used to configure the remote identifier used for authentication. When this field is blank, the value in the Remote Host field will be used.
|
| Local Network | This field is used to configure the local network that will be reachable from hosts on the other side of the IPsec VPN. |
| Remote Network | This field is used to configure the remote network that will be reachable from hosts on the local side of the IPsec VPN. |
| Shared Secret | This field should contain the shared secret or PSK (pre-shared key) that is used to authenticate the connection, and must be the same on both sides of the tunnel for the connection to be successful. Because the PSK is actually used as the encryption key for the session, using long strings of a random nature will provide the highest level of security. |
| DPD Interval | The number of seconds between R_U_THERE messages. Enter 0 to disable this feature. |
| DPD Timeout | The number of seconds for a dead peer tunnel to be restarted. |
| Ping Address | The IP address of a host on the remote network to ping for verifying that the tunnel is connected and routing. Leave blank to disable. |
| Ping Interval | The time in minutes between ping attempts of the ping address. Leave as 0 to disable. Recommended value is 1 when using a Ping address. |
| Authentication and SA/Key Exchange | If you leave the Phase 1 and Phase 2 manual configuration checkboxes disabled, IPsec will attempt to automatically negotiate the encryption protocol with the remote peer when creating the tunnel. Given the number of different IPsec implementations and versions, as well as the overall complexity of the protocol, best results can often be achieved by enabling manual configuration of these two options, and selecting Encryption, Hash, DH Key Group, and Lifetime values that exactly match the settings configured on the peer device. |
Reports
The Reports tab provides a view of all reports and events for all connections handled by WireGuard VPN.
Reports
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
Pre-defined report queries: {{#section:All_Reports|'WireGuard VPN'}}
The tables queried to render these reports:
Related Topics
WireGuard VPN FAQs
How resilient is a WireGuard connection?
WireGuard is built for roaming. If your device changes networks, e.g. from WiFi to a mobile/cellular, the connection will persist because as long as the client sends correctly authenticated data to the WireGuard VPN server, the server keeps the connection alive.
What cryptography is used in WireGuard?
WireGuard uses several ciphers including ChaCha20, Curve25519, BLAKE2s, SipHash24, and HKDF. For more details refer to the WireGuard Protocol & Cryptography documentation.
What transport protocol and port does WireGuard use?
WireGuard encapsulates and encrypts all data using UDP with default port 51820. There is a built-in access rule to allow WireGuard traffic on this port.