UPnP: Difference between revisions
(→UPnP) |
No edit summary |
||
| (4 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
<span style="display:none" class="helpSource network_upnp">UPnP</span> | <span style="display:none" class="helpSource network_upnp">UPnP</span> | ||
<span style="display:none" class="helpSource network_advanced_upnp">UPnP</span> | |||
== Feature deprecated! == | |||
Please note that UPnP support has been removed as of NG Firewall v17.3. This page is being left up for those using older versions of NG Firewall. | |||
== About UPnP == | == About UPnP == | ||
| Line 12: | Line 16: | ||
UPnP settings can be found at '''Config > Network > Advanced > UPnP'''. | UPnP settings can be found at '''Config > Network > Advanced > UPnP'''. | ||
| Line 20: | Line 21: | ||
These are considered "automatic port forward rules" and therefore you should consider the potential security implications before enabling in your environment. In a home environment with an Xbox, you probably want it enabled. In an office environment, you likely do not want it enabled at all. | These are considered "automatic port forward rules" and therefore you should consider the potential security implications before enabling in your environment. In a home environment with an Xbox, you probably want it enabled. In an office environment, you likely do not want it enabled at all. | ||
== Settings == | == Settings == | ||
| Line 34: | Line 32: | ||
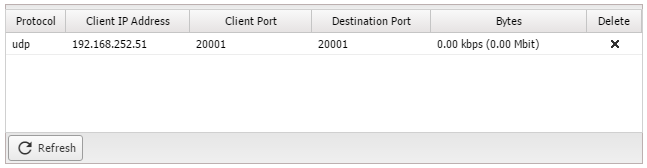
* '''UPnP Status''' is a status readout of recent activity. The statistics are reset at reboot and when settings are saved. | |||
[[Image:upnp_status.png|center|frame|UPnP Status]] | |||
=== Access Control Rules === | |||
These rules allow you to control which networks can use UPnP as well as the ports they can manage along with an allow or deny action. All rules are processed in order. | |||
The default rules for Allow all and Deny all allow all UPnP traffic if UPnP is enabled. | |||
If you which to control access to a particular network, create a new Allow rule for that network and ports and make sure it is above the Deny all rule. | |||
Latest revision as of 17:20, 14 February 2025
Feature deprecated!
Please note that UPnP support has been removed as of NG Firewall v17.3. This page is being left up for those using older versions of NG Firewall.
About UPnP
Universal Plug and Play (UPnP for short) allows clients to create their own firewall port forward rules. Common uses include:
Allow gaming consoles to host games. Enable BitTorrent clients to host uploads.
UPnP settings can be found at Config > Network > Advanced > UPnP.
Security Considerations
These are considered "automatic port forward rules" and therefore you should consider the potential security implications before enabling in your environment. In a home environment with an Xbox, you probably want it enabled. In an office environment, you likely do not want it enabled at all.
Settings
This section reviews the different settings and configuration options available for QoS.
- Enabled: Controls whether UPnP is enabled or disabled. The default setting is unchecked, which means UPnP is disabled.
- Secure Mode: An option that restricts port creations to the client system. In most environments you should leave this enabled.
- UPnP Status is a status readout of recent activity. The statistics are reset at reboot and when settings are saved.
Access Control Rules
These rules allow you to control which networks can use UPnP as well as the ports they can manage along with an allow or deny action. All rules are processed in order.
The default rules for Allow all and Deny all allow all UPnP traffic if UPnP is enabled.
If you which to control access to a particular network, create a new Allow rule for that network and ports and make sure it is above the Deny all rule.