NG Firewall Virtual Appliance on VMware: Difference between revisions
From Edge Threat Management Wiki - Arista
Jump to navigationJump to search
Bcarmichael (talk | contribs) |
|||
| (12 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
NG Firewall can be installed as a virtual appliance in VMware for use in production environments or for learning and demonstration purposes. | |||
=== Getting Started === | |||
: | Requirements: | ||
# VMware ESX server version 6.5.0 Update 3 or newer | |||
# One virtual NIC and vSwitch per NG Firewall Interface | |||
== | ==== Download the NG Firewall installer ==== | ||
1. Log into your [https://launchpad.edge.arista.com/ Edge Threat Management] account. | |||
2. Click GET STARTED > Software Downloads at the top right-hand corner. | |||
3. Download either version of the installer. Note that both options install the same software, however the "Serial" version uses only a command-line interface. | |||
==== Deploy image to ESX server ==== | |||
* Open your VMware vSphere Client and login to your server. | |||
* Create a new virtual machine and point the CD-Rom to the NG Firewall ISO image. | |||
* Configure the CPU and RAM per the [[Hardware Requirements]] guidelines. | |||
* In the “Ready to Complete” screen, verify that everything looks OK and click “Finish” | |||
==== Configure Physical NIC to vSwitch mappings ==== | |||
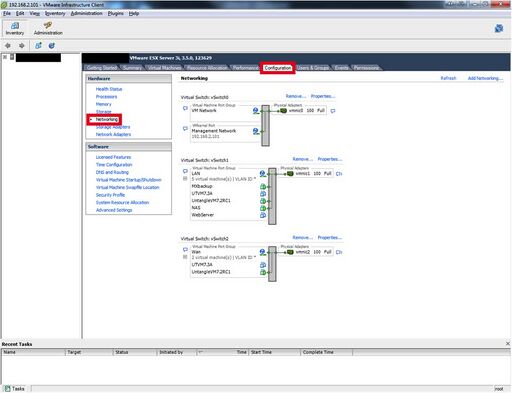
* Setup/confirm your vSwitch Settings. Click on the ESX host, then select “Configuration" tab and "Hardware -> Networking” | |||
[[Image:vm19.jpg|none|512px|vCenter Hardware->Networking]] | |||
* It is best practice to place your “Management Network “ is on a own vSwitch. (This is not a Must but if you can make sure that NG Firewall does not exist on the same vSwitch as any Management Interface) | |||
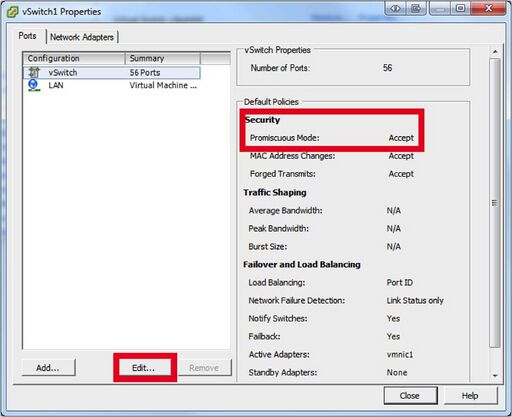
* On the vSwitches that NG Firewall will connect to activate “promiscuous mode” click on “Properties…” | |||
* Ensure that Promiscuous has status “Accept” otherwise hit "Edit" and go to the “Security “ Tab and change “Reject” to “Accept”. You will need to do this on all vSwitches that NG Firewall Virtual Machine connects to! | |||
[[Image:vm21.jpg|none|512px|vCenter vSwitch Properties2]] | |||
==== Configure the Virtual Machine for your Network ==== | ==== Configure the Virtual Machine for your Network ==== | ||
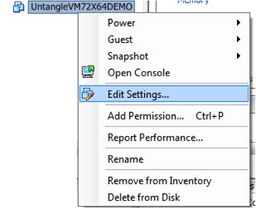
* Right click on the new Virtual Machine and select “Edit Settings”. | * Right click on the new Virtual Machine and select “Edit Settings”. | ||
[[Image: | [[Image:vm15.jpg|none|256px|vCenter Edit Settings]] | ||
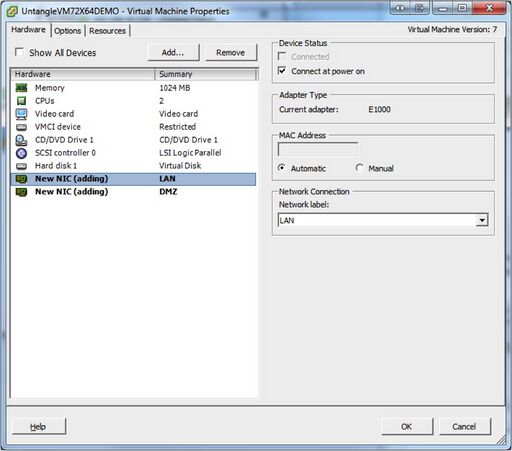
* You will need to add new virtual NICs and connect them to the appropriate vSwitches. Warning! Two Bridged Interfaces to the same vSwitch will crash your ESX server. Each | * You will need to add new virtual NICs and connect them to the appropriate vSwitches. Warning! Two Bridged Interfaces to the same vSwitch will crash your ESX server. Each NG Firewall NIC should be connected to its own vSwitch. Each vSwitch should be connected to it's own Physical NIC, or at least be separated by VLAN tagging at the physical NIC level. | ||
* In this example, you can see that the new NICs are connected to different vSwitches labeled LAN and DMZ. | * In this example, you can see that the new NICs are connected to different vSwitches labeled LAN and DMZ. | ||
[[Image: | [[Image:vm17.jpg|none|512px|vCenter VM properties]] | ||
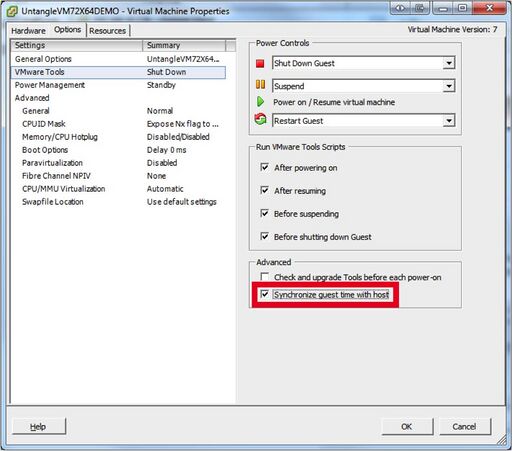
* Under “Options”->“VMware Tools” make sure to check the “Synchronize guest time with host” and click "OK" | * Under “Options”->“VMware Tools” make sure to check the “Synchronize guest time with host” and click "OK" | ||
[[Image: | [[Image:vm18.jpg|none|512px|vCenter VM properties/tools options]] | ||
Latest revision as of 15:59, 24 July 2024
NG Firewall can be installed as a virtual appliance in VMware for use in production environments or for learning and demonstration purposes.
Getting Started
Requirements:
- VMware ESX server version 6.5.0 Update 3 or newer
- One virtual NIC and vSwitch per NG Firewall Interface
Download the NG Firewall installer
1. Log into your Edge Threat Management account. 2. Click GET STARTED > Software Downloads at the top right-hand corner. 3. Download either version of the installer. Note that both options install the same software, however the "Serial" version uses only a command-line interface.
Deploy image to ESX server
- Open your VMware vSphere Client and login to your server.
- Create a new virtual machine and point the CD-Rom to the NG Firewall ISO image.
- Configure the CPU and RAM per the Hardware Requirements guidelines.
- In the “Ready to Complete” screen, verify that everything looks OK and click “Finish”
Configure Physical NIC to vSwitch mappings
- Setup/confirm your vSwitch Settings. Click on the ESX host, then select “Configuration" tab and "Hardware -> Networking”
- It is best practice to place your “Management Network “ is on a own vSwitch. (This is not a Must but if you can make sure that NG Firewall does not exist on the same vSwitch as any Management Interface)
- On the vSwitches that NG Firewall will connect to activate “promiscuous mode” click on “Properties…”
- Ensure that Promiscuous has status “Accept” otherwise hit "Edit" and go to the “Security “ Tab and change “Reject” to “Accept”. You will need to do this on all vSwitches that NG Firewall Virtual Machine connects to!
Configure the Virtual Machine for your Network
- Right click on the new Virtual Machine and select “Edit Settings”.
- You will need to add new virtual NICs and connect them to the appropriate vSwitches. Warning! Two Bridged Interfaces to the same vSwitch will crash your ESX server. Each NG Firewall NIC should be connected to its own vSwitch. Each vSwitch should be connected to it's own Physical NIC, or at least be separated by VLAN tagging at the physical NIC level.
- In this example, you can see that the new NICs are connected to different vSwitches labeled LAN and DMZ.
- Under “Options”->“VMware Tools” make sure to check the “Synchronize guest time with host” and click "OK"