Local Users: Difference between revisions
No edit summary |
Bcarmichael (talk | contribs) |
||
| (2 intermediate revisions by one other user not shown) | |||
| Line 4: | Line 4: | ||
''Local Users'' stores a list of users that can be used by the applications. | ''Local Users'' stores a list of users that can be used by the applications. | ||
For example, [[Captive Portal]] can use the local directory to authenticate users. | For example, [[Captive Portal]] and [[OpenVPN]] can use the local directory to authenticate users. | ||
{{BiScreenshot|config|local-directory}} | {{BiScreenshot|config|local-directory}} | ||
To add new users click on the Add button. You must supply a username, first name, last name, email address, and password. Only the | To add new users click on the Add button. You must supply a username, first name, last name, email address, and password. Only the administrator can set the password for a given user. Users can be imported or exported using the import/export buttons on the upper right. | ||
An expiration date can be specified for a user. If the expiration date has passed that user will no longer be authenticated. | An expiration date can be specified for a user. If the expiration date has passed that user will no longer be authenticated. | ||
To use the Local Directory, | To use the Local Directory, configure apps such as [[Captive Portal]] and [[OpenVPN]] to authenticate against the Local Directory while requiring user authentication. | ||
'''WARNING:''' Typically, when passwords are stored, password hashes are saved and the original cleartext password is forgotten so administrators do not have access to user passwords. However, The passwords for users are stored in the local directory are stored in cleartext because some applications and features (L2TP) depend on access to the cleartext password. Administrators do have access to cleartext user passwords and caution is advised. | == MFA and OpenVPN == | ||
You can enable TOTP based multi factor authentication for OpenVPN client connections. When adding a user, select '''Enable MFA for OpenVPN''' and click '''Generate new key'''. | |||
[[Image:local_directory_mfa.png|500px|center|Local Directory User MFA]] | |||
After generating a key, click the gear icon to show the QR code. Use the generated code in any TOTP mobile app such as Google Authenticator. The TOTP app generates a temporary that the user enters into their OpenVPN client. | |||
'''Note:''' You must also enable MFA for client configurations in [[OpenVPN]]. | |||
[[Image:local_directory_mfa_code.png|500px|center|Local Directory User MFA]] | |||
'''WARNING:''' Typically, when passwords are stored, password hashes are saved and the original cleartext password is forgotten so administrators do not have access to user passwords. However, The passwords for users that are stored in the local directory are stored in cleartext because some applications and features (L2TP) depend on access to the cleartext password. Administrators do have access to cleartext user passwords and caution is advised. | |||
Latest revision as of 22:38, 7 May 2021
Local Users
Local Users stores a list of users that can be used by the applications. For example, Captive Portal and OpenVPN can use the local directory to authenticate users.
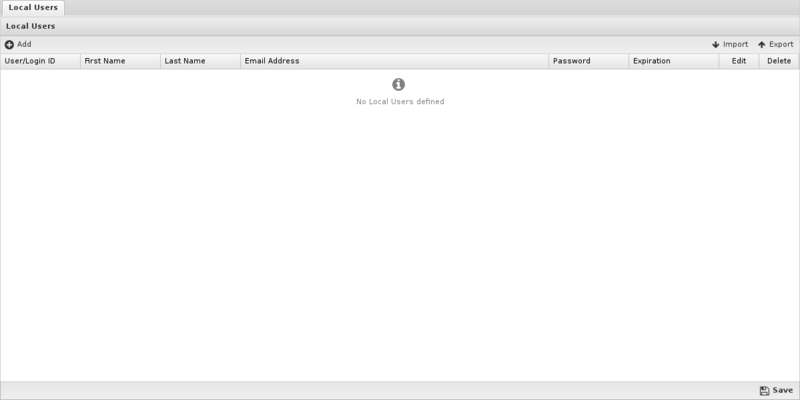
To add new users click on the Add button. You must supply a username, first name, last name, email address, and password. Only the administrator can set the password for a given user. Users can be imported or exported using the import/export buttons on the upper right.
An expiration date can be specified for a user. If the expiration date has passed that user will no longer be authenticated.
To use the Local Directory, configure apps such as Captive Portal and OpenVPN to authenticate against the Local Directory while requiring user authentication.
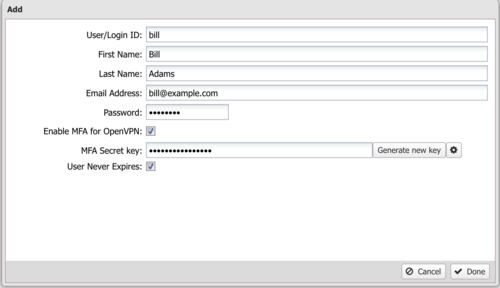
MFA and OpenVPN
You can enable TOTP based multi factor authentication for OpenVPN client connections. When adding a user, select Enable MFA for OpenVPN and click Generate new key.
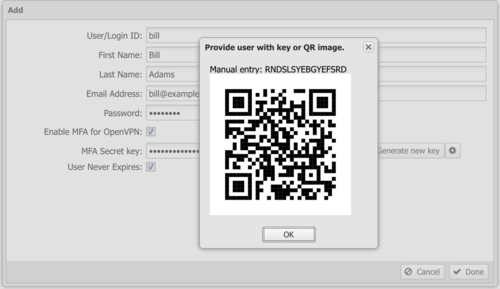
After generating a key, click the gear icon to show the QR code. Use the generated code in any TOTP mobile app such as Google Authenticator. The TOTP app generates a temporary that the user enters into their OpenVPN client. Note: You must also enable MFA for client configurations in OpenVPN.
WARNING: Typically, when passwords are stored, password hashes are saved and the original cleartext password is forgotten so administrators do not have access to user passwords. However, The passwords for users that are stored in the local directory are stored in cleartext because some applications and features (L2TP) depend on access to the cleartext password. Administrators do have access to cleartext user passwords and caution is advised.
